The FBI. Cybercrime Division or International Cyber Security Protection Alliance infection is a variant of ransomware from the Urausy family. When installed this ransomware does not allow you to access your computer or your files without a paying the fake fine. When infected with this Trojan, you will be shown a ransom screen instead of your Windows desktop when you login to Windows.
This ransom screen will state that the FBI has detected that your computer has been downloading or distributing copyrighted content or pornography. This infection will display different lock screens depending on what country your computer is currently located in. It is able to detect your country by using the IP address of your computer. This guide will focus on the USA variant of the FBI Cybercrime Division, but the removal guide can be used for any variant of this ransomware.
The message displayed by the threat can be localized depending on the user’s location, with text written in the appropriate language.

FBI Cybercrime Division Ransomware
FBI. Cybercrime Division
International Cyber Security Protection AllianceIP: xxx.xxx.xxx
Country: US United States
Region:
City:
ISP:
Operating System: : Your Country Here
Username:Attention!
Your PC is blocked due to at least one of the reasons specified below.You have been violation Copyright and Related Rights Law (Video, Music, Software) and illegally using or distributing copyrighted content, thus infringing Article I, Section 2, Clause 8, also known as the Copyright of the Criminal Code of United States of America.
Article I, Section 2, Clause 8 of the Criminal Code provides for a fine of 200 to 500 hundred minimal wages or a deprivation of liberty for 2 to 8 years.
You have been viewing or distributing prohibited Pornographic content (Child Porn/Zoophilia and etc). Thus violating article 2, Section 1, Clause 2 of the Criminal Code of United States of America. Article 2, Section 1, Clause 2 of the Criminal Code provides for a deprivation of liberty for 4 to 12 years.
Illegal access to computer has been initiated from your PC, or you have been…
without your knowledge or consent, your PC may be infected by malware, thus you are violating the law of Neglectful Use of Personal Computer. Article 210 of the Criminal Code provides for a fine of up to $100,000 and/or a deprivation of liberty for 4 to 9 years.
Pursuant to the amendment to the Criminal Code of United States of America of August 28, 2012, this law infringement (if it is not repeated – first time) may be considered as conditional in case you pay the fine to the State.
<Lot’s of further pretend legal nonsense followed by>
Fines may be paid within 72 hours after the infringement. As soon as 72 hours elapse, the possibility to pay the fine expires, and a criminal case is initiated against you automatically within the next 72 hours!
To unblock the computer, you must pay the fine through MoneyPak or MoneyGram xpress Packet of $300.
When you pay the fine, your PC will get unlocked in 1 to 72 hours after the money is put into the State’s account.
Since your PC is unlocked, you will be given 7 days to correct all violations.
FBI Cybercrime Division Ransomware [removal]
Please download HitmanPro to your desktop.
Press this link for the complete “User Manual” for HitmanPro.Kickstart.
- Start the program by double clicking on HitmanPro.exe. (Windows Vista/7 users right click on the HitmanPro icon and select run as administrator).
- Click on the “HitmanPro.Kickstart” button to create a bootable USB-stick with HitmanPro.Kickstart (see the screenshot below).

- Now insert the USB flash drive that you will use to write the HitmanPro.Kickstart files to.
- As soon as one or more USB flash drives are detected, a selection screen will be presented.

- Now select the USB flash drive on which you want to place the HitmanPro.Kickstart files and press the button Install Kickstart.
- Important! Be aware that that all contents of the selected flash drive will be erased before the HitmanPro.Kickstart files are written.
- If you press the ‘Yes’ button now, the selected USB flash drive will be formatted and all necessary HitmanPro.Kickstart files will be retrieved from the HitmanPro servers and written to the flash drive

- Once the process is completed you can now remove the USB flash drive from the PC and use it to remove the malware from a ransomed PC.
- Now insert the HitmanPro.Kickstart USB flash drive into a USB port of the ransomed PC and start the PC.
- During the startup of the PC, enter the (BBS) Bios Boot Selector menu with F10 or F11 and select the USB flash drive that contains HitmanPro.Kickstart to boot from.
- If it’s not possible to enter the BBS go into the BIOS and set the USB option as your first boot-device by the boot-sequence.
- The default way to boot is option 1, which skips the master boot record of your hard drive. If you do not press any key, the process will continue after 10 seconds using the default boot selection.

- If you see a logon screen you can either select a user and logon, or if you wait approximately 15 seconds, HitmanPro will be started on your Windows logon screen.

- Click on the next button. You must agree with the terms of EULA.
- Check the box beside “No, I only want to perform a one-time scan to check this computer“.
- Click on the next button.
- The program will start to scan the computer. The scan will typically take no more than 2-3 minutes.
- Click on the next button and choose the option activate free license
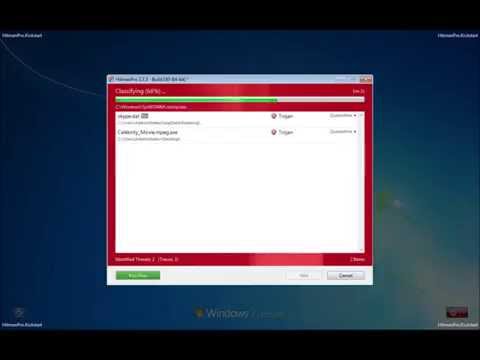
- Click on the next button and the infections where found will be deleted.
- Click now on the Save Log option and save this log to your desktop.
- Click on the next button and restart the computer.
Alternative instructions
Start your computer in Safe Mode with Networking and scan for malware with Malwarebytes Anti-Malware.
- Remove all CDs, and DVDs from your computer, and then restart your computer.
- Press and hold the F8 key as your computer restarts.Please keep in mind that you need to press the F8 key before the Windows start-up logo appears.
Note: With some computers, if you press and hold a key as the computer is booting you will get a stuck key message. If this occurs, instead of pressing and holding the “F8 key”, tap the “F8 key” continuously until you get the Advanced Boot Options screen. - On the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

- If your computer has started in Safe Mode with Networking, you’ll need to perform a system scan with Malwarebytes Anti-Malware
Download Malwarebytes Anti-Malware to your desktop.
- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware
- Then click Finish.
- If an update is found, it will download and install the latest version.
- Once the program has loaded, select Perform quick scan, then click Scan.
- When the scan is complete, click OK, then Show Results to view the results.

- Be sure that everything is Checked (ticked) except items in the C:\System Volume Information folder and click on Remove Selected.
- If you accidently close it, the log file is saved here and will be named like this: C:\Documents and Settings\Username\Application Data\Malwarebytes\Malwarebytes’ Anti-Malware\Logs\mbam-log-date (time).txt
- Note: If MBAM encounters a file that is difficult to remove, you will be presented with 1 of 2 prompts.
- Click OK to either and let MBAM proceed with the disinfection process.
- If asked to restart the computer, please do so immediately. Failure to reboot will prevent MBAM from removing all the malware.
- After the restart in Normal mode, start Malwarebytes Anti-Malware again and perform a Full System scan to verify that there are no remaining threats.
FBI Cybercrime Division Ransomware video
Incoming search terms:
- ransomware removal
- webserches
- fbi cybercrime division firefox
- fbi cybercrime division google chrome
- how remove webserches a virus
- webserches remove
